Automate vulnerability assessment
Perform vulnerability scans of your IT assets on a regular basis to effectively manage your cyber risk.

Automate vulnerability assessment
Perform vulnerability scans of your IT assets on a regular basis to effectively manage your cyber risk.

Scan for 100k+ potential security issues
Identify the weakest links
Defining which of your IT assets demand your team’s primary attention is challenging. Scan to get the most out of your cyber risk management efforts.
Stay ahead of adversaries
Find vulnerabilities in your IT infrastructure before attackers can exploit them. Regular internal and external scans accelerate your daily security work.
Scan all types of IT assets
Protect your cloud and on-premise IT and IoT devices, networks, systems, and applications. Don’t fix single vulnerabilities but their root causes.
Utilize threat intelligence
Exploitable cyber threats quickly evolve into multistage attacks. Benefit from daily updates of your scan engine and keep up with newest issues.
Our clients feel the difference


"We found Autobahn Security to be best-in-class among vulnerability assessment platforms. The Autobahn platform allows us to scan our large internet footprint and provides clear, concise reporting with easy-to-follow remediation instructions."
Ariel Pizetsky
VP of IT and Cyber

“Something which really caught our eye about Autobahn were the Cyber Fitness Workouts, which provide you with an estimate of how much your remediation actions will reduce overall hacking risk.”
Vivdha Singh
VP of Security at ng-voice

"Autobahn‘s scalability aligns with the envisioned growth for our company, helping us to achieve our (security) goals."
Ayman Matter
IT Director & Security Officer at ESIM Chemicals3 Steps for effective vulnerability assessment
1. Scan natively or integrate
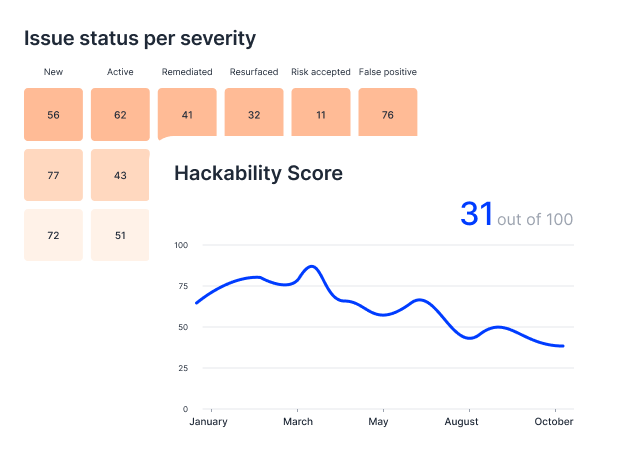
2. Review your scan results
Check your dashboard or download scan reports. But don’t dwell on the issues as we provide you the solutions.
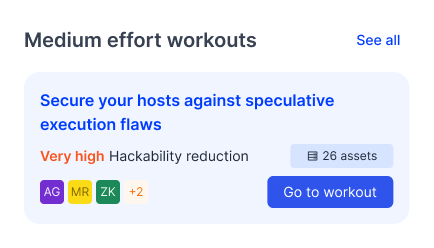
3. Move on to remediation
Start Fixing with Cyber Fitness Workouts
Autobahn Fit automatically groups your issues by their root cause, then maps them to fixes, Cyber Fitness Workouts, that address the common origin of each issue group.
- Receive a prioritized list of Cyber Fitness Workouts
- Get your issues re-assessed with threat intel
- Ask for on-demand false positive checks
- Lower false positives with statistical methods
Ready to assess?
Let's go!



