Vulnerability Remediation Made Fast
This blog post tells you how you can speed up your remediation management process using Autobahn Security’s Cyber Fitness Workouts, with another core benefit of making cybersecurity understandable to the non-security IT experts on your team.
5+1 things to know about Cyber Fitness Workouts
Having issues with remediation measures being too complex or time-consuming to implement? The easiest way to show why the workouts matter is to provide a glimpse into how we create them. The amount of our work that goes into writing the workouts roughly equals the time your organization can save when mitigating cyber risks.

Your IT/cybersecurity team will love our workouts. Here’s what we do to make the life of your IT professionals easier:
- Research multiple technical sources
- Analyze, restructure, and simplify complex technical procedures to turn them into a few user-friendly steps
- Shorten many official documentation sources
- Enrich official documentation with alternative approaches
- Create remediation steps if they do not exist
- Verify fixes and remediations
Imagine this scenario: You’re on a sailing trip in the middle of the ocean. (In German, we call it “Segeltörn.“), and you’re in control:
- Weather conditions are optimal. You checked the wind forecast using the most reliable apps.
- You’ve prepared well for the adventure to make a hassle-free sailing trip possible:
- Checked your apps and you know how deep the water is.
- Downloaded the maps, so now you know where the major obstacles are.
- Ensured anchoring goes smoothly. Anchoring your yacht in busy bays is now as easy and stress-free as it can be. With maps and apps, finding anchorages is a breeze.
What makes this experience unique? You’ve guessed it by now. Someone has to do the preparatory work first, and then you can sail away to exciting destinations.
Similarly, we at Autobahn Security create workouts for a plain-sailing experience when you need to update or harden your systems against multiple cyber flaws. We digest oceans of information for you to enjoy a hassle-free remediation procedure.
Here’s what we do with the available content when creating workouts.
“No action without research”: All documentation sources deserve attention, but our customers get the short list
How do our customers get the most compelling remediation suggestions?
Here’s what a working day looks like as a technical writer at Autobahn Security. The team prioritizes topics to write about based on data analysis about the most relevant workouts. To keep things interesting, the core question is this:
“What do our customers need to fix or remediate today?”
Once the vulnerabilities to be fixed are identified, extensive research begins. Tech writers work closely with cybersecurity engineers and remediation experts. Together they put on a steersman’s cap to determine the sailing course and analyze charts for underwater obstacles. Then it’s the tech writer’s responsibility to write the workout, maintain the sailing course, and do more research along the way. Once the mission is accomplished, cybersecurity engineers and remediation experts review and verify the new workout (of which more later), doing even more research if required.
“Simplicity is the ultimate sophistication”: Let us analyze, restructure, and simplify
Leonardo da Vinci was right: “Knowing is not enough; we must apply”. And for a broader target audience to apply a technical procedure efficiently, it must be simple. Here is what we do to our workouts if we suspect that it is not simple enough:
Rephrase
Deleting a few instances of technobabble often works miracles. Instead of googling for meaning, you can jump straight into the task.
Replace a chunk of text with a label
For example, a chunk of 3-4 sentences presented as one step in a tutorial receives a concise description that summarizes the aim of the technical adventure the user is up to. There is always a concrete goal we are trying to achieve in a particular step. Are we determining the software version for future patch management? Or maybe verifying the success of the previous steps? Or creating a backup? We just need to know. And once we’ve found it out, we pass it on to you dear readers. The remediation steps instantly become more readable.
Restructure
A misplaced warning may cost you dear. We all want to be warned about potential technical issues before, not after we have experienced them. We do not want to overlook an important alert in a wall of text. We want to take informed decisions, not just click through a task.
In our Cyber Fitness Workouts, we make sure all the caveats, dangerous choices, and “if…else” clauses are visible in the UI and presented at the right moment to give readers enough time to react and optimize.
Ensure progressive disclosure
It’s a fact supported by user research: when we are given just enough information to do an activity, we perform better. There’s less confusion and more sense of purpose. UX writers and designers know it well.
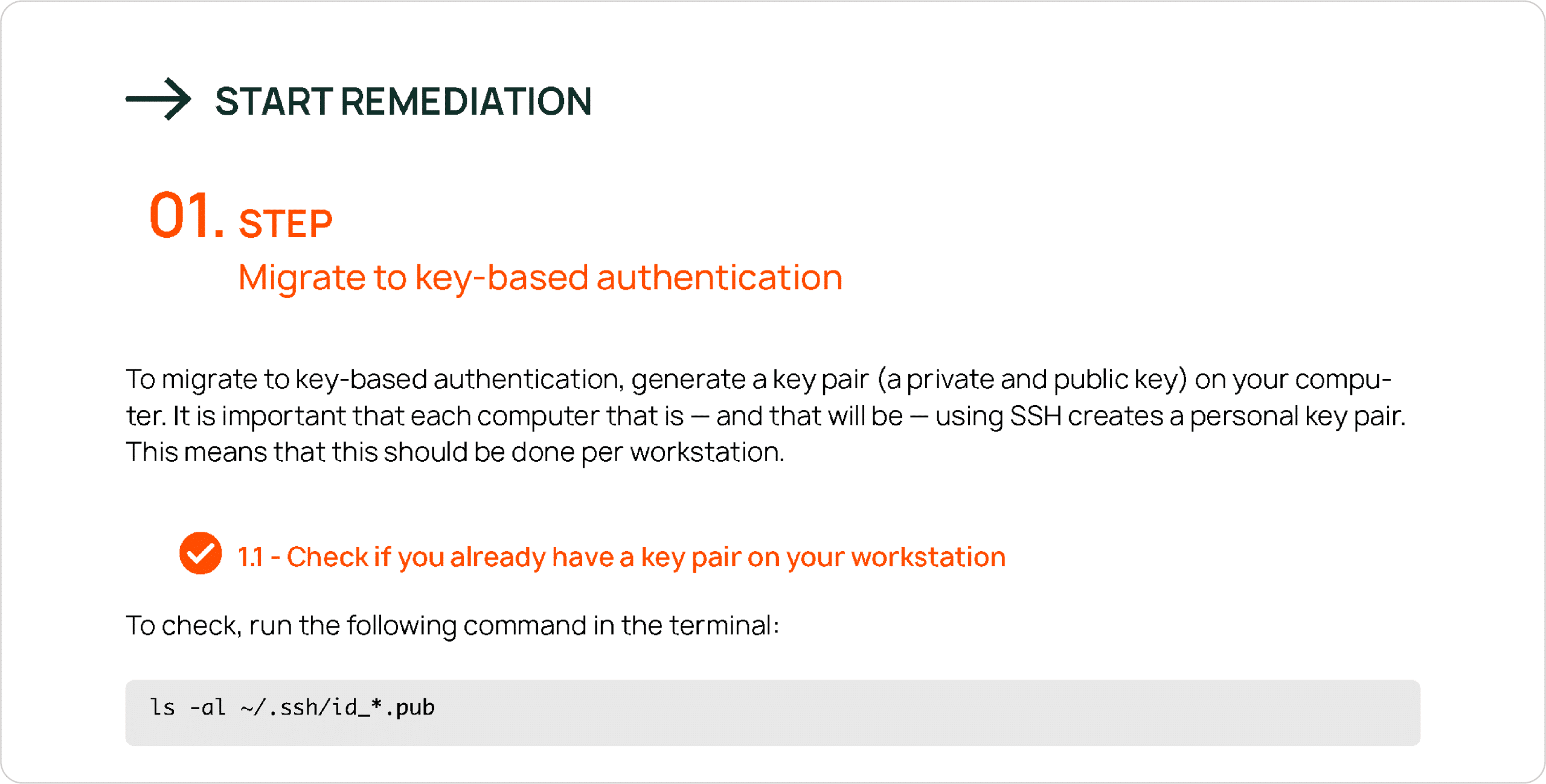

“Brevity is the sister of talent”: Some documentation sources just need to be shortened
In digital content management, the idea that information must be concise is an axiom. The much dreaded “tl;dr” abbreviation, short for “too long; didn’t read”, explains succinctly the anguish of being ignored based on the length of your contribution.
However, it may still be a debatable topic how much documentation is enough to get a job done. Many organizations are simply used to having thorough user manuals and developer guides spanning hundreds of valuable (!) pages. While there are cases when you appreciate the level of detail, there are also scenarios when you just need to get your patching and hardening tasks done swiftly and efficiently.
You might not have the time to search for the relevant chapter in several manuals. We understand. Just let us do it for you. (We eat software manuals for breakfast.)
In our experience, remediations and fixes go much faster if you get a digest version. If done properly, the “less is more” principle applies to software documentation just fine.
We at Autobahn Security are learning to walk the fine line between saying enough to be useful and not saying to
o much to get you bogged down in details. It’s like reefing the sails on a small boat when the wind gets too strong. It takes time to get used to it.
And since we are at it, do let us know if you think there is room for improvement. With your valuable feedback, we get better at the information architecture of our Cyber Fitness Workouts, and you get cyber fit faster. It’s a win-win situation.
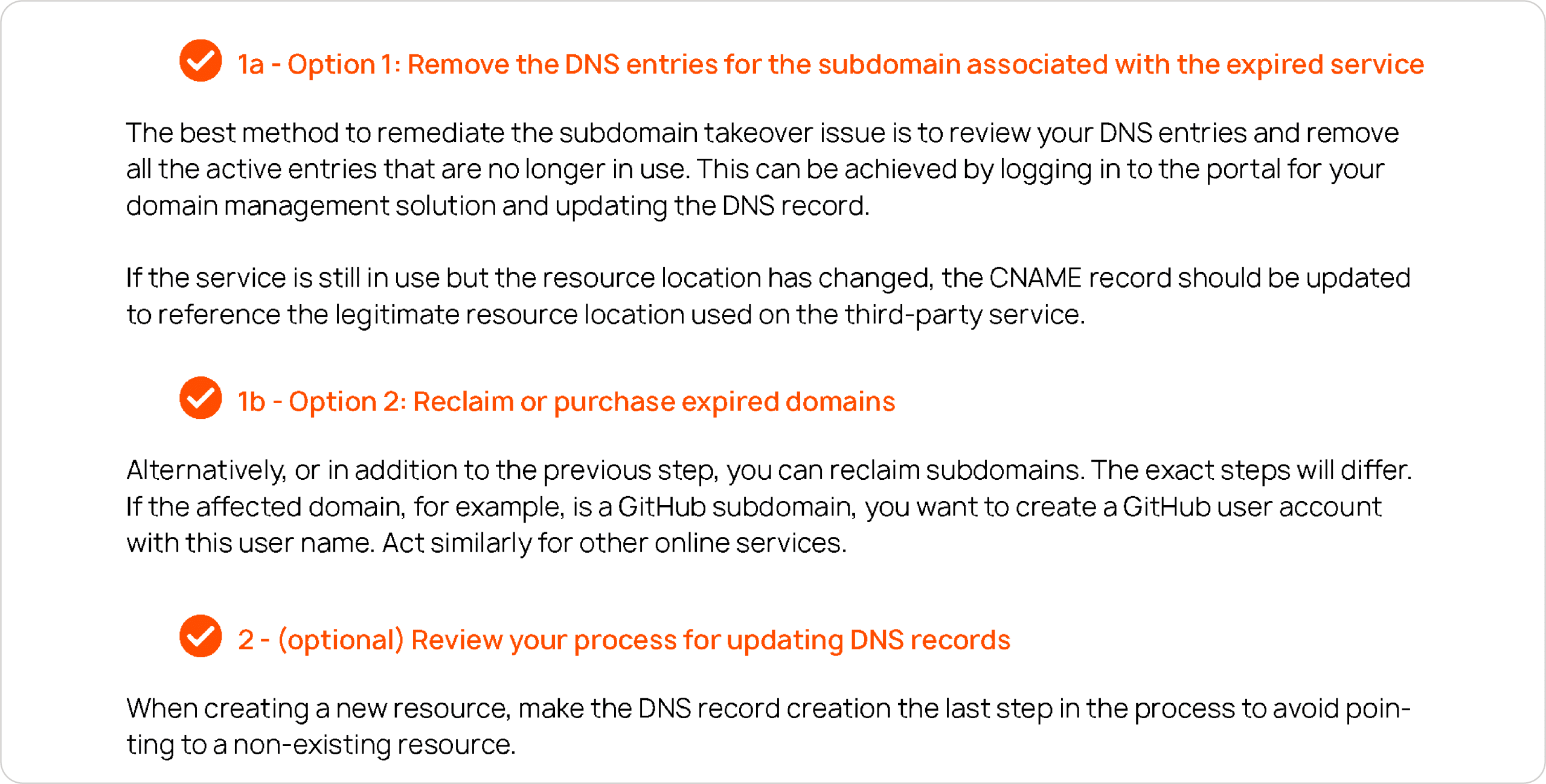

“Trust but verify”: Let us enrich the documentation
Technically minded people often do a great deal of research and analysis to investigate new approaches, caveats, troubleshooting measures, and similar vital bits of information. Why blindly trust everything you can find in a piece of software documentation? There is a vibrant community of like-minded people bursting with confidence to tell you how exactly you solve a particular software issue. To engage in a technical discussion is often the way to go in case official documentation omits a few caveats, contains mistakes, or was found inefficient in a particular use case.
It’s often quite helpful to know what the experienced IT professionals at stackoverflow.com or similar Q&A platforms are saying about a particular remediation suggestion. This is often the fastest way to find out in what way remediation option 1 differs from remediation options 2 and 3. And we are always happy to pass it on to you for a plain-sailing experience. No doubt, you can google the tricky IT topics too, but it often makes sense to delegate. We do IT research with passion and dedication. And we want you to have a hassle-free voyage.
“If something doesn’t exist, we’ll invent it”: We create remediation steps
You’ve searched high and low but haven’t found how to update or harden a particular system. Does it ring a bell?
Chances are we’ve been through this and have listed a few useful steps for you. We never hesitate to go the extra mile, even if it means translating a particular set of steps from a foreign language we do not know yet.
It’s like pausing our sailing adventure for a diving mission. Finding pearls and bringing treasures we are lucky to find underwater is very rewarding.
“Let us be the depth gauge on your boat”: We verify the remediation steps
Software development and quality assurance (QA) go hand in hand like the sea chart and the depth gauge on your boat.
A depth gauge is a device that tells you the real depth of water, warning you, for example, that the boat might collide with an obstacle in a second. What if the sea chart tells you that the depth should be ok?
If you’re like us, you go with the depth gauge because of its hands-on approach. A sea chart is only an abstraction. It might be outdated, like any guide or user manual. As technology changes quickly, all the relevant descriptions must be revisited, verified, and reviewed regularly.
We at Autobahn Security have a set of workout acceptance criteria that help us manage the verification process. What can be verified gets verified. It means someone runs the commands in a test environment and controls the results. And the person does so several times depending on the number of operating systems involved and the number of remediation options included in a workout.

About Autobahn Security
Autobahn Security is a SaaS platform that saves IT security experts time and empowers IT teams to make networks more secure. Our platform aggregates, filters and prioritizes vulnerabilities from different scanners and turns them into easy-to-understand remediation guides. Autobahn Security has been created as a result of decades of combined experience in white hat hacking and security consulting for Fortune 500 companies. Autobahn is trusted by companies across different industries in over 20 countries, including Allianz, SwissPost and Taboola.
Read in this blog how simple vulnerability management can be made.

How you get started and what you can expect from us within just 1 week
- Understand your issue remediation process and pain points
- Walk through the key aspects of the platform
- Set up scans
- Evaluate scan results

Request a free expert discussion right now
We evaluate your individual challenges, schedule a demo session, provide an overview of our value process, and discuss potential milestones and next steps. Talk to our team to see how Autobahn Security can make you cyber-fit!


