In today's increasingly digital world, security threats are becoming more and more sophisticated. One such threat that can cause serious harm to individuals and businesses alike is a zero-day vulnerability. In this article, we'll explore what zero-day vulnerabilities are, the…

To effectively shield your organization from cyber attacks, it's vital to understand cyber attack vectors. After all, how do you know what you should be doing to defend, if you don’t have an idea of the threats?But what are cyber…

New vulnerabilities and attack vectors emerge almost daily. Defense teams have a higher chance of fending off attacks when there is less time between hackers' active exploitation and detection. While SRLabs conducts research on both vulnerabilities (e.g., reverse engineering, black…

The increasing functionality of smart speakers also leads to a growing attack surface for hackers. In 2019 research by SRLabs unveiled two scenarios hackers might abuse both Alexa or Google Home to spy on users. The vulnerability allows third parties…
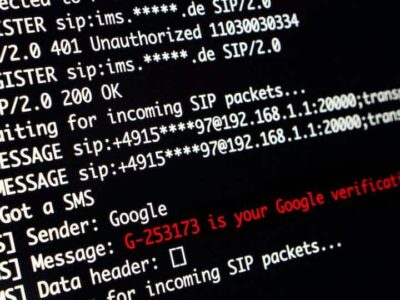
In 2019, Google and several mobile operators started implementing a new communication technology, Rich Communication Services (RCS) [1]. RCS replaced traditional calling and SMS, serving as their replacement in the communication landscape. The technology included also new messaging possibilities and…

Phishing is the attempt to steal sensitive data through tricking a person into revealing passwords or credit card data or downloading a computer virus. In a particularly unlucky scenario, phishing may become a triple loss, as the victims lose their…

Threats and vulnerabilities are on the rise. But many companies are not aware of their security level. Read in this article how your Hackability Score prioritizes issues for your IT team and why you benefit fourfold from just 1 single…

The topic of hacking guarantees exciting Hollywood moments. In the real world, however, we are making little progress on hacking prevention. Both for the same reason: The actions of hackers seem to be mysterious because most people know little about…
