Why could you measure Hackability as a KPI in cybersecurity? Cyber security has recently gained significantly in importance for businesses. In its annual Cyber Security Breaches Survey, the UK Department for Digital, Culture, Media and Sport (DCMS) found that 82% of boards and senior management consider cybersecurity a high priority issue. (To put it in perspective, it is a 5-percent increase compared to 2021). The risk of IT infrastructure breaches is crearly a topic frequently discussed in boardrooms and other high level meetings. Yet according to a 2021 Navisite study, 55% of US companies do not employ a Chief Information Security Officer (CISO). The same study found that in 60% of companies the cybersecurity strategies are not in the hands of a dedicated security team.
IT and security experts should not rely on senior management to understand the technicalities of their IT infrastructure and its vulnerabilities. Instead, the information needs to be provided in a way that helps managers to keep abreast of the latest trends in vulnerability management and to understand their corporate risks. While security tools do a great job at detecting vulnerabilities, they traditionally have been built for security experts and fail to cater to the needs of other decision makers. To bridge this gap, we have introduced a new metric, the Hackability Score, that enables companies to measure their hackability, compare their organization to others, and track their progress with one easy-to-understand KPI.
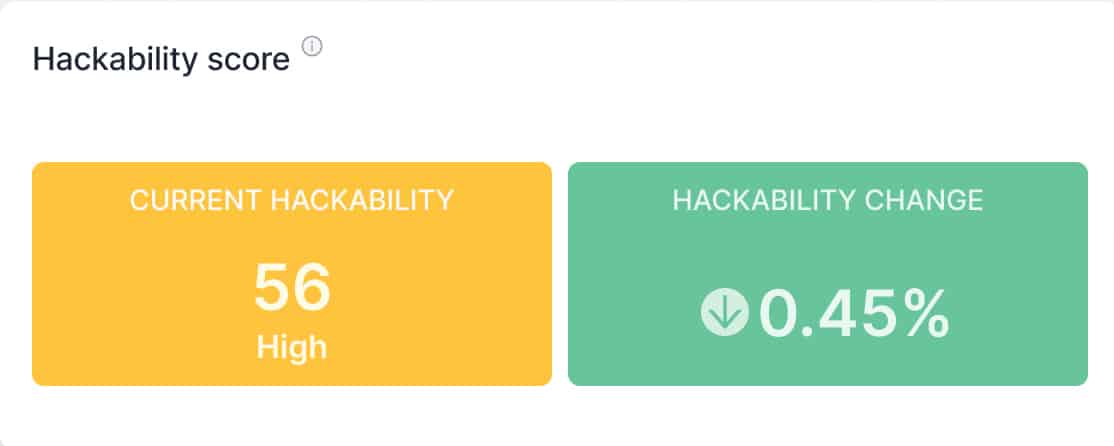
The Hackability Score: Making security measurable
The Hackability Score summarizes all the vulnerabilities an organization exposes to hackers in one single score. Its introduction makes it significantly easier for both security experts and nonexperts to understand the overall risk an organization faces. As part of a continuous process, it enables teams and organizations to make their efforts measurable and track their progress. Like all KPIs, having a KPI in cybersecurity helps teams speak a common language.
Whoever has used a vulnerability scanner at least once will know the following scenario. You scan your IT landscape for vulnerabilities, but once the result has come in your team feel overwhelmed by the sheer amount of issues found. Large organizations can be confronted with up to a million or more findings – hardly a number you want to be thrown around in a board meeting. To make it worse, the resulting tasks need to fit into the already tight schedules of notoriously understaffed IT departments.
But what these reports do not consider is how critical these issues actually are or whether the same issue was discovered more than once. This is where our Hackability Score comes into play.
What types of issues are considered?
The Hackability Score involves all issues that might be detected by cybersecurity scanners. Besides our own scanning capabilities, the Autobahn Security Cyber Fitness Platform includes access to Qualys’ vulnerability scanner. Additionally, our software has integrations with many other major scanners, such as Rapid7, Tenable, or Nessus.
The four common issues regarding information security are:
- Issues in a company’s identity and access management, like weak credentials and missing authentication
- Unnecessary exposure of IT assets to the Internet
- Insufficient asset hardening due to configuration issues
- Outdated software signals, for example, due to lacking patch management
The Hackability Score does not include any information on areas like social engineering awareness that might be a result of internal training or endpoint security.
How do customers use our Hackability Score?
The Autobahn Security Hackability Score finally provides one KPI to measure and track IT security. The most common use cases among our customers are:
- Tracking IT security progress
- Benchmarking to compare the organization with competitors and set goals
- Reporting to stakeholders
- Evaluating vendors and suppliers
Tracking progress
Autobahn Security is all about making cybersecurity manageable. Many cybersecurity or IT teams in general still track their progress by looking at the amount of issues resolved or the overall amount of vulnerabilities left or found. But this approach does not give any indication on how critical closing a specific issue is for your business. It also doesn’t reflect the entire prioritization process when deciding which issues to resolve first.
What can be more demoralizing than to close a series of tasks only to realize that your list of issues has merely changed from 9,999 to 9,990. Let’s move on from looking only at the output and start working towards actual outcomes.
The Hackability Score does exactly that. It not only shows how well your company’s protection is against outside attacks but also how your hackability improves over time.
Benchmarking
Autobahn Security continuously analyzes different industries all over the world and enables companies to compare themselves to their peers, other industries, or even the entire market.
To gain an even better understanding of their situation, we automatically benchmark our customers to comparable companies. This way we put your results into perspective showing wether your are more or less likely to be the target of hackers.
Benchmarking is also a useful tool when setting targets as it enables companies to see what realistic goals for their industry and company size are.
Reporting
We already dived into this topic at the beginning that having a clear KPI to report and work with can empower IT experts to do more than just report to senior management.
Does any of these scenarios sound familiar?
- You’ve done your homework, but your ticket gets stuck in a jammed backlog
- Despite the C-levels commitments, (sufficient) budgets don’t get approval
- You want to update an asset, but the affected teams refuse to accept any downtime as everything is “still working smoothly”
You probably have many more stories like these. It would be a tedious task finding a company with a single employee who does not operate your IT Infrastructure in one way or another. There are probably only a few departments with as many stakeholders within any company.
Obviously internal challenges do not just magically disappear. What you can do is equip yourself with the right tools and data to face them. You can offer your stakeholders an intuitive way to assess the situation and measure the impact of counteractions. The right vulnerability management strategy is possibly the strongest weapon in any business context to prevent data breaches and other adverse cyber events.
Evaluating
Hopefully we never stop learning – and one thing we have learned in recent years is how critical and complex supply chains are. Blocking 13% of all global trade or disrupting supply chains by a worldwide pandemic is not an everyday event.
Unfortunately cyber attacks are an everyday security call – with at least 88% of companies reporting they faced some sort of attack in 2019 (Proofpoint).
Inevitably any company will be the target of cyber criminals at some point and there is not much we can do about that. But what we can do is make sure that we are not a defenseless target – and that includes having a resilient supply chain. Many companies, especially in highly regulated industries, might already have a requirement to do so.
For both sides this provides an opportunity.
- By incorporating cyber security as part of your supply chain management, you do not just protect your own IT infrastructure. You harden your entire business model.
- Suppliers and vendors that proactively support cyber risk assessments and report their hackability can gain access to new markets and create competitive advantages.
According to the Department for Digital, Culture, Media and Sport, only 13% of UK businesses review their immediate suppliers for potential cybersecurity risks. However, for 44% of large companies and 34% of all companies in the finance and insurance industry this is already a common practice.
How exactly does our Hackability Score help?
The most common reason (36%) why companies do not review cyber risks in their supply chain is a lack of time and money. The Hackability Score allows companies, with the permission of their suppliers, to use scanning data to gain an overview of the hackability in their supply chain. Suppliers and vendors, on the other hand, are provided with a metric they can proactively share with their (potential) customers.
The Hackability Score is just a reflection of your cybersecurity and a small part of the Autobahn Security Cyber Fitness Platform. If you want to know more about how Autobahn Security can help your company elevate cybersecurity to the next level while saving resources, you should take a look at our Cyber Fitness approach or schedule a demo to get to know our solution first hand.

