Threats and vulnerabilities are on the rise. But many companies are not aware of their security level. Read in this article how your Hackability Score prioritizes issues for your IT team and why you benefit fourfold from just 1 single KPI. Sounds interesting? In a free expert meeting, we evaluate your individual challenges and provide an overview of our process and potential next steps.
The problem: How to deal with unprioritized cybersecurity issues
Ensuring security begins with knowing and limiting your vulnerabilities. The most common ones include:
- Outdated software
- Unsecured APIs
- Weak user credentials
- Little to no access control
- Misconfigurations
- Poor or no data backup
- Poor network segmentation
You will need to scan for vulnerabilities, and remediate discovered ones, regularly. The challenge: they’re not all created equal. Some pose a bigger threat than others.
But scanners usually treat all vulnerabilities the same. That’s why IT security teams often begin going through the findings one by one and address them to the best of their abilities. Some vulnerabilities, like weak passcodes, can be quickly resolved. Others, like poor network configuration, may require more time and cooperation with other departments.
Soon, you realize the budget you had allocated to these tasks may not be enough. To make things worse, after days of work, barely 25% of vulnerabilities have been resolved. You have no idea if the remaining vulnerabilities pose more or fewer risks than the others. And you may also need to justify the budget needs to the management board.
Save up to 90% of time spent on remediation management
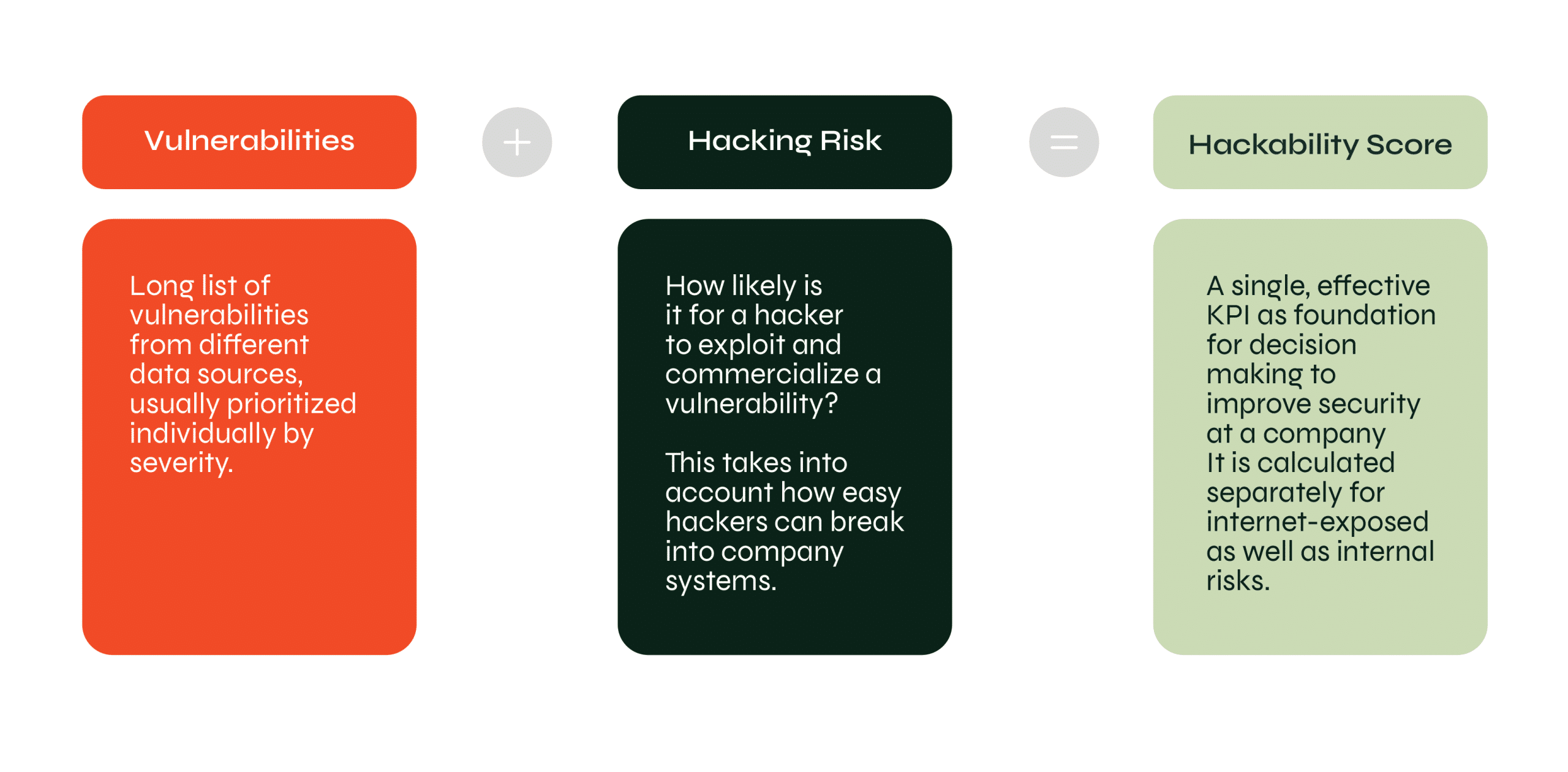
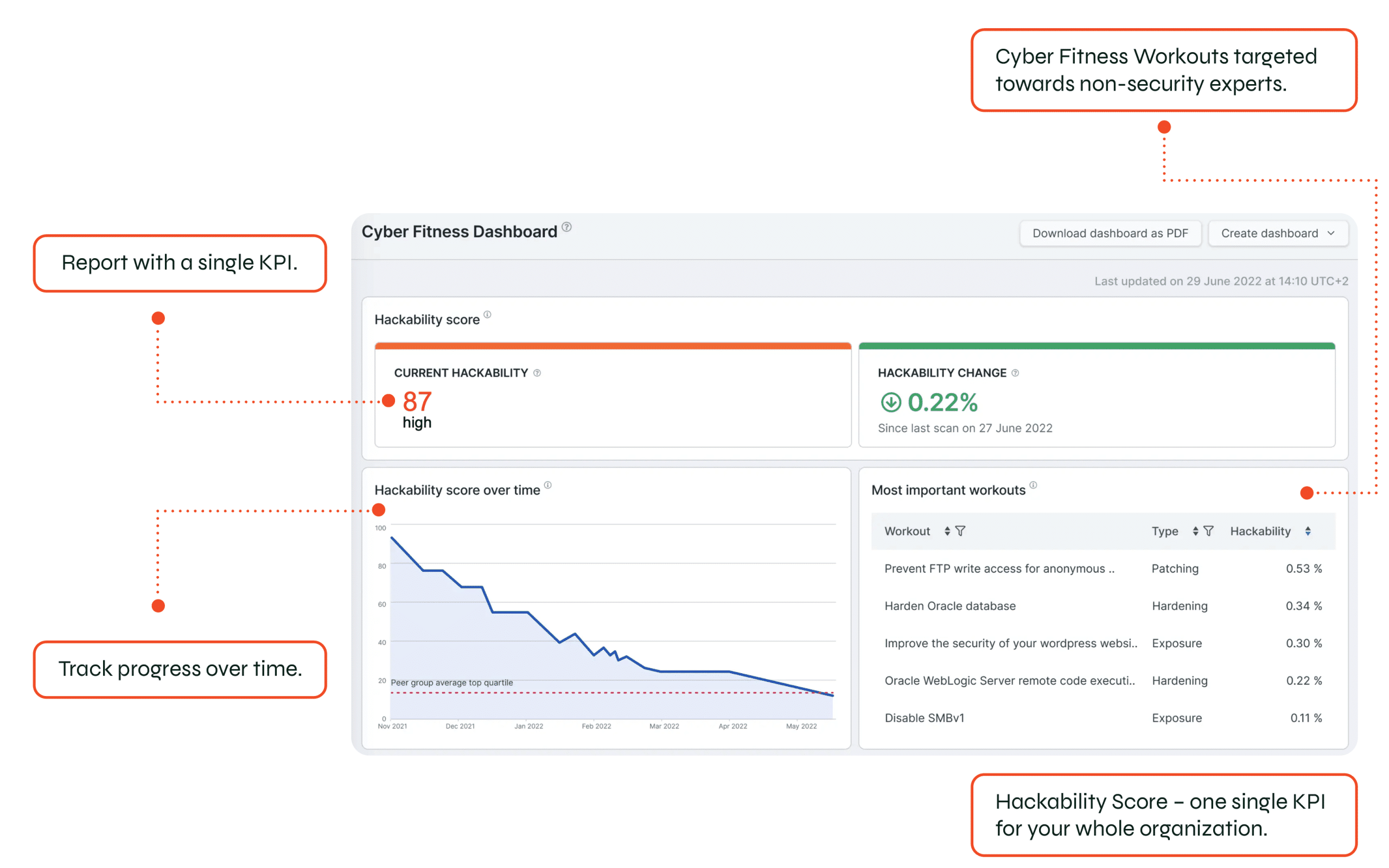
The Hackability Score summarizes available information about how exactly and how easily hackers can break into company systems. It provides a clear and concise view of an organization’s security posture. You need to have it because knowing, for instance, 5,000 vulnerabilities, isn’t necessarily an indicator of how hackable you are.
The Hackability score takes the gravity of each issue into account and prioritizes it automatically. This saves up to 90% of time spent on remediation management. Instead of a long list of vulnerabilities, this score looks at organization-wide assets and returns a single KPI that summarizes the risks.
The score is then normalized based on the number of exposed services to compare organizations of different sizes. It also points to actionable steps that help increase your resilience.
4 reasons to use the Hackability Score
There are 4 main areas where the Hackability Score is useful:
Tracking progress
Fixing some vulnerabilities may seem like progress. But what if the ones you fixed were the ones that posed no risks anyway? Instead, by looking at the Hackability Score, tracking progress is much easier. Is the score lower? Then you made good progress.
Reporting
While 82% of senior management consider cybersecurity a priority, explaining necessary investments may still be an issue. The Hackability Score helps discuss the issues and needs in a clear, concise manner. You don’t have to worry that your partners aren’t cybersecurity savvy. These reports will be easy to understand.
Benchmarking
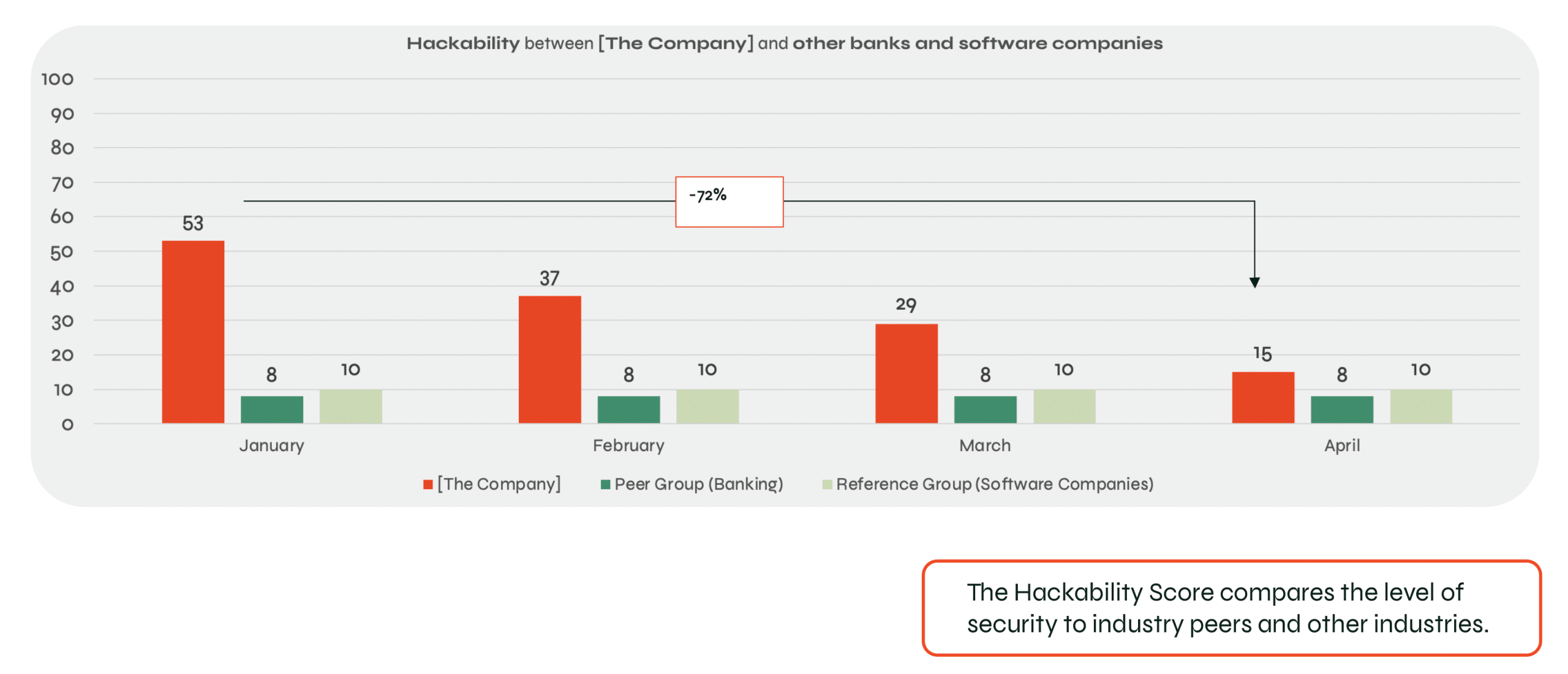
As Autobahn Security analyzes various industries all over the world, companies can easily compare themselves against their peers. It’s useful when trying to set realistic goals and expectations. You can analyze the results of similar companies both in terms of industry and size. That way you can have a clear picture of what to expect for cybersecurity.
Assess your supply chain
When running a business, you’ll likely need to collaborate with various suppliers and vendors. Depending on how you work together, at some point, their weaknesses could become your weaknesses. That’s why it’s important to incorporate cybersecurity in the supply chain as well. Calculating your suppliers’ Hackability Score is a quick way to assess the risks. Of course, you’ll need their permission. But that should be easy enough to obtain.
How you get started and what you can expect from us within just 1 week
- Understand your issue remediation process and pain points
- Walk through the key aspects of the platform
- Set up scans
- Evaluate scan results
Request a free expert discussion right now
We evaluate your individual challenges, schedule a demo session, provide an overview of our value process, and discuss potential milestones and next steps.
Talk to our team to see how Autobahn Security can make you Cyber Fit.

