Autobahn Fit7 steps to boost your hacking resilience
7 jobs to boost your hacking resilience
with Autobahn Fit

Autobahn Fit serves as a single pane of glass that fully automates the aggregation and prioritization of vulnerabilities from any security assessment tools, turning them into easy-to-understand remediation guides. Following our maxims to make vulnerability management impactful, easy, measurable, and personal, here’s how we improve your cybersecurity in 7 simple steps:
Discover and connect your assets
By combining these data sets, we reach a close approximation of the IT infrastructure and the software components running in your network, which provides the foundation for the next step in vulnerability management.
Consolidate your vulnerabilities
Consolidate assets and vulnerability data from pentests, vulnerability scanners, and other expert tools to get an initial idea of your potential cyber risks – and in case you don’t have a scanner license, feel free to use our powerful scanning engine included in your package.
Although no scanner can single-handedly cope with all prevailing technologies, the good news is that Autobahn Security aggregates raw data not only from one, but from a multitude of assessment tools.
Assess vulnerabilities
Our experts eliminate false positives and irrelevant findings, enriching the relevant vulnerabilities with additional information. The vulnerabilities then get reclassified concerning the severity level . Seen from a hacker’s perspective: how do vulnerabilities contribute to hacking and exploitability? What’s the potential impact?
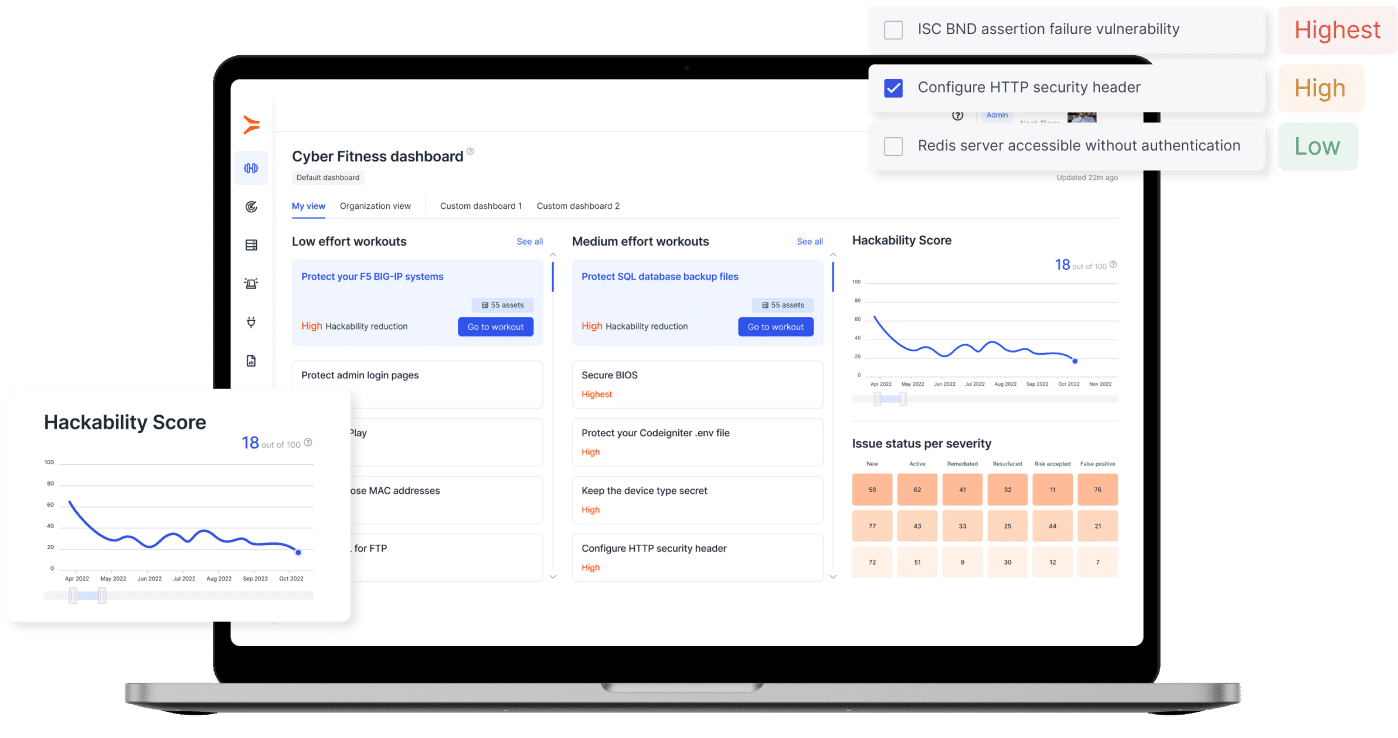
This information computes into Autobahn Security’s Hackability Score – our actionable hacking risk metric that gives you a measurable overview of your security posture.
Cluster common root causes
Map root cause clusters to remediation guides
Our security experts and technical writers do all the research work for you, putting actionable instructions in understandable words. We automate cyber security know-how for your in-house team.
Hundreds of our ready-to-use remediation guides are waiting to lead you through your remediation processes – and their number is growing. Implement our easy-to-understand and actionable guides for patching, hardening, and exposure reduction, and soon you’ll continue focusing on making your business thrive.
Prioritize your Cyber Fitness Workouts
To ensure you always work on the most impactful guides, we show you how each Workout reduces your Hackability Score. Ranked from highest to lowest, you immediately know what to work on first, and what to do next.
Support your remediation
Based on your efforts and our support, an efficient vulnerability management is established and successfully operates in your company. This not only allows peers to keep track of your cyber security posture, encouraging them to keep up, but also enables you to share valuable insight with the board regarding benchmarking.
Discover and connect your assets
Understanding your company’s attack surface leads to determining which of your assets need to be protected, monitored, and maintained. Connecting Cloud assets (AWS, Azure, GCP) and inventory tools (CMDB), and performing asset discovery scans, ensures that all your assets are up to date. By combining these data sets, we reach a close approximation of the IT infrastructure and the software components running in your network, which provides the foundation for the next step in vulnerability management
Consolidate your vulnerabilities
Consolidate assets and vulnerability data from pentests, vulnerability scanners, and other expert tools to get an initial idea of your potential cyber risks – and in case you don’t have a scanner license, feel free to use our powerful scanning engine included in your package. Although no scanner can single-handedly cope with all prevailing technologies, the good news is that Autobahn Security aggregates raw data not only from one, but from a multitude of assessment tools.
Assess vulnerabilities
Our security engineers continuously assess vulnerabilities, seamlessly updating Autobahn Security’s issue-database on a regular basis. The issue-database forms the growing intel of our prioritization engine, which is the foundation for steps 4 to 6.
Our experts eliminate false positives and irrelevant findings, enriching the relevant vulnerabilities with additional information. The vulnerabilities then get reclassified concerning the severity level. Seen from a hacker’s perspective: how do vulnerabilities contribute to hacking and exploitability? What’s the potential impact? This information computes into Autobahn Security’s Hackability Score – our actionable hacking risk metric that gives you a measurable overview of your security posture.
Cluster vulnerabilities with common root causes
Just like eliminating false positives and irrelevant findings, clustering vulnerabilities with the same root cause is an essential step on the way to automated prioritization and remediation. Because all vulnerability clusters with the same root-cause can be fixed with 1 single remediation. A very effective way to expedite your remediation process.
Map vulnerability clusters to remediation guides
To efficiently reduce your workload, even the largest amount of cyber security vulnerabilities is mapped and turned into a small number of easy-to-follow remediation guides, our Cyber Fitness Workouts. Now, any IT team can remediate vulnerabilities, even without security expertise. Our security experts and technical writers do all the research work for you, putting actionable instructions in understandable words. We automate cyber security know-how for your in-house team. Hundreds of our ready-to-use remediation guides are waiting to lead you through your remediation processes – and their number is growing. Implement our easy-to-understand and actionable guides for patching, hardening, and exposure reduction, and soon you’ll continue focusing on making your business thrive.
Prioritize your Cyber Fitness Workouts
After our platform mapped your issues to our signature Cyber Fitness Workouts – our easy-to-understand remediation guides – we look at the contribution of each Workout to your company’s Hackability Score. To ensure you always work on the most impactful guides, we show you how each Workout reduces your Hackability Score. Ranked from highest to lowest, you immediately know what to work on first, and what to do next.
Support your remediation
To reassure you as much as possible during your vulnerability management processes, we’re offering full support until your relevant security issues are closed. If you have questions, we’ll answer. If you’re stuck, we’ll hear your call. Even if you’re encountering a suggested remediation guide for the first time – our team will stand by until you’ve succeeded in implementing it. Based on your efforts and our support, an efficient vulnerability management is established and successfully operates in your company. This not only allows peers to keep track of your cyber security posture, encouraging them to keep up, but also enables you to share valuable insight with the board regarding benchmarking.
The Hackability Score – how attracted are hackers to you?
The Hackability Score shows the severity of your vulnerabilities as seen from a hacker’s perspective. It accurately reflects hacking risks across your network environment, continuously adjusted by including newly discovered issues. The Hackability Score summarizes the security posture of all your assets into one single number, allowing you to easily track improvement, benchmark, and report to stakeholders. Our Cyber Fitness Workouts – Autobahn Security’s signature remediation guides – are automatically prioritized according to their anticipated Hackability reduction.
Talk to our team, now, to see how Autobahn Security can make you cyber-fit.
Let Autobahn Security be your personal cyber fitness coach. For quick and sustained improvement, we recommend following our Cyber Fitness Workouts regularly. Track your performance increase and you’ll see: the more you exercise our workouts, the cyber-fitter you’ll get.

Autobahn Fit License Packages
Our flexible pricing is based on the number of active IPs. Discover and compare our plans.
Remediation guides
1 integration
Custom dashboard
3 Integrations
Annual benchmark
Unlimited integrations
25 custom workouts/year
Custom integrations